-

Cyber Strategy: Defense-in-Depth
The chart here presents an illustrative guide to the multi-layered strategy known as “Defense-in-Depth” as a 3D pyramid with different levels, each representing a distinct layer of security measures and policies, underscoring the complexity and comprehensiveness required for effective cybersecurity defense. At the top of the pyramid is “Governance & Risk Management,” which emphasizes the…
-

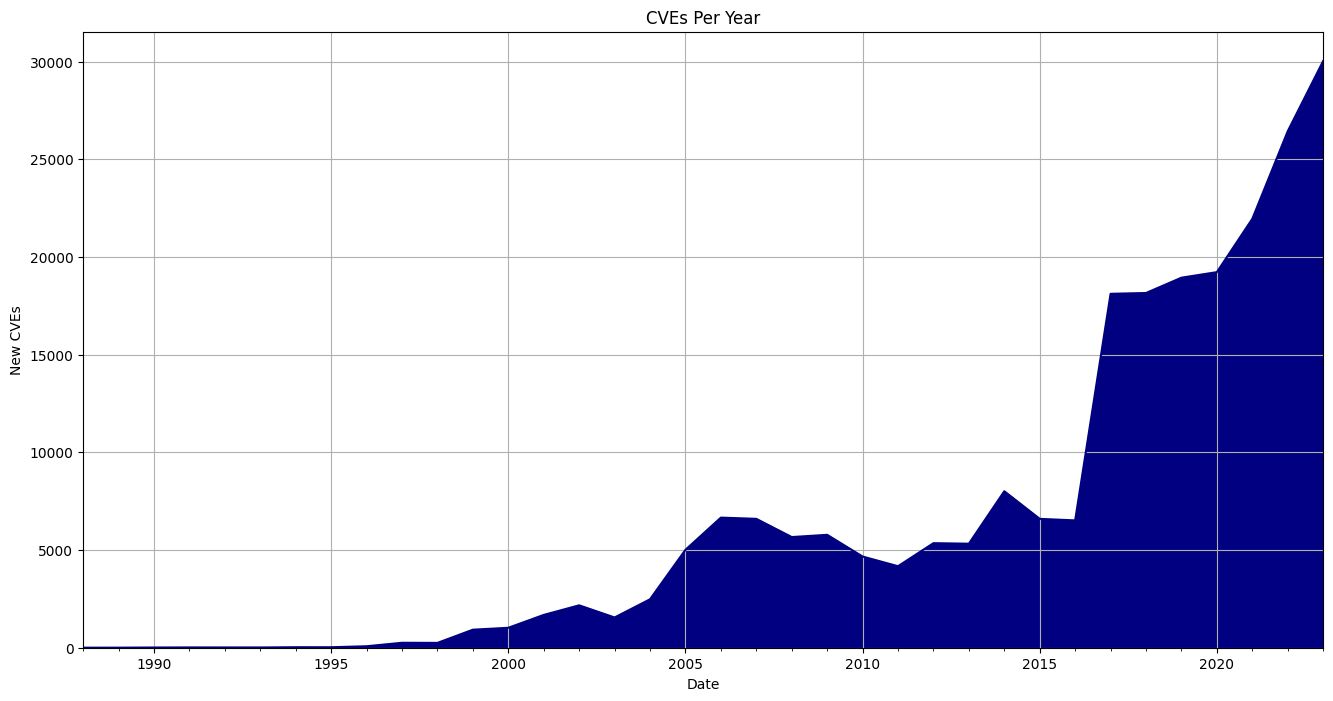
Rising Tides of War
Cybersecurity has become an increasingly critical concern for businesses and individuals alike. With the rise of sophisticated cyber threats, it has become essential for organizations to implement robust vulnerability management practices. This includes vulnerability tracking, attack surface management, and continuous scanning methods. In this article, we will explore each of these aspects in detail, highlighting…
-

Know your enemy.
Vulnerability assessment and penetration testing have gained high importance especially in the last couple of years. Organizations often have a complex network of assets storing sensitive data. Such assets are exposed to potential threats from inside as well as from outside the organization. To get an overview of the security posture of the organization, conducting…
-

Defining “Threat Management”…
Proactive Data Defense Use our robust cybersecurity solution designed to proactively safeguard your digital assets using SecAI. Our platform continuously monitors the digital landscape, ensuring that emerging threats are identified and mitigated promptly using SecAi and integration of the world’s top security data enrichment APIs with our next-generation attack surface monitoring platform. Our suite of…
-

Simplifying Cyber Security
ZEPSEC helps your business stay safe from online threats. Our service watches over your digital world, alerting you to any dangers before they become problems. We offer everything you need to keep your business safe online: Plays well with others… check. Calculates and mitigates risk… check. Perfect for Small Businesses Simple and Powerful Features Empower…
-

The Dawn of SecAI
SecAI is the integration of artificial intelligence into cybersecurity practices, which enables organizations to more quickly identify vulnerabilities, detect and mitigate potential attacks, and improve incident response. This technology is revolutionizing cybersecurity solutions by continuously learning and adapting to new threats and empowering organizations to combat modern cyber threats effectively. AI combines human-like intelligence with…
-

The Future is NOW: Security SaaS trends in 2024
In recent years, SaaS has become essential for corporate IT, serving as the foundation for service businesses like medical practices, law firms, and financial services firms. Non-service businesses, such as manufacturers and retailers, also heavily rely on cloud-based software. These applications store various types of data, ranging from general corporate information to highly sensitive intellectual…
-

Achieving More Effective Risk Management
The repeated warnings from CISA and the Biden Administration regarding the Russian cyber threat have put US agencies and businesses on high alert. They are expecting retaliatory cyberattacks from Russia in response to the Ukrainian aid package. The Biden Administration’s budget proposal for FY2023 emphasizes the importance of cybersecurity for the federal government. This increased…
-

Understanding Breaches: The Incident Response Playbook
Introduction to Incident Response in the Dark Web EraCyber Threat Intelligence (CTI) plays a crucial role in incident management, especially when dealing with Dark Web breaches. Utilizing the NIST Framework, we can outline the Dark Web monitoring lifecycle into seven distinct stages: Preparation, Detection, Analysis, Containment, Eradication, Recovery, and Post Activity. This guide delves into…