-

Human Vulnerability: “The Devil is in all of you!”
Why people are much more vulnerable than computers… The danger of phishing attacks is significant and they are constantly becoming more sophisticated. Phishing attacks are a type of psychological manipulation employed by hackers to deceive people into disclosing sensitive information or taking actions that put their security at risk. Despite advancements in technology that have…
-

Wartime Cyber Insurance: Mitigate Risks, Not Threats
In the words of former FBI director, Robert Mueller, “There are only two types of companies: those that have been hacked and those that will be.” This reality, combined with increased awareness and frequency of cyber attacks, has led to a rise in cyber insurance. The percentage of insurance clients opting for cyber coverage has…
-

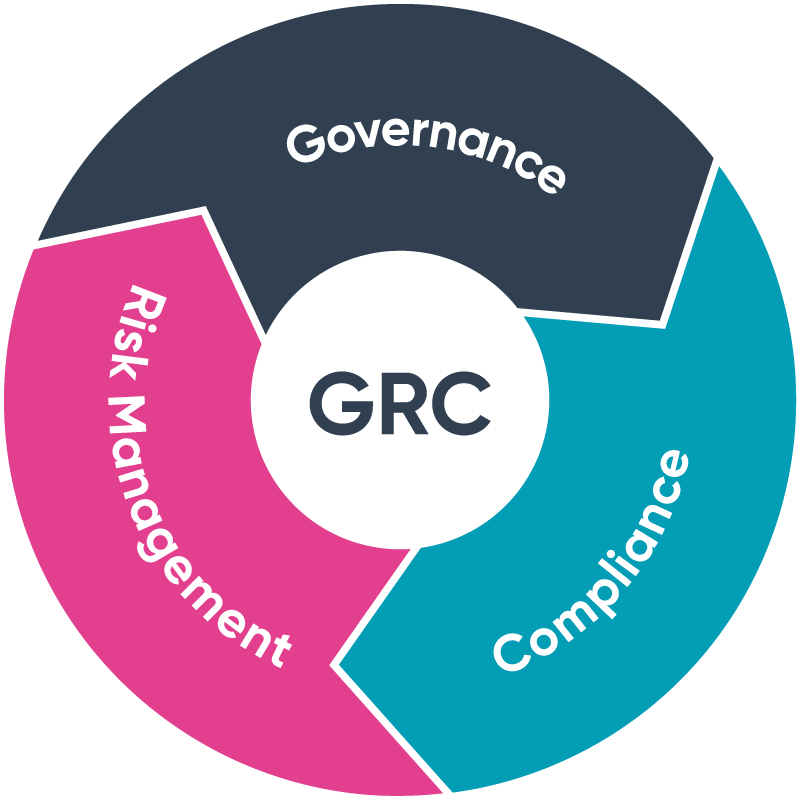
Introduction to GRC: Governance, Risk, and Compliance
🎓 What is Security GRC? The security GRC field is covering lots of ground and include a varied number of tasks and responsibilities. Some of them will sound exciting, some will reignite painful memories. 💂♂️ Governance Governance, as the name implies, focuses on how security is managed and its oversight. This could include building the…
-

Increasing Cyber Attacks On Accounting Firms
The July 15 tax filing deadline is finally behind you. Now is the perfect time to address the growing number of cyberattacks still taking place in the accounting industry. Many accounting practices are reporting that IT vendors and employers rushed to provide access for remote employees without fully understanding how to properly implement and secure…
-

-

Real-Time Protection: Continuous Scanning
Threats are dynamic and evolving at a rapid pace, making it imperative to implement robust security measures and strategies. One such measure is Continuous Attack Surface Testing (CAST), a modern, proactive approach to cyber security. This article aims to provide a comprehensive understanding of CAST, its importance, working, benefits, and why it is becoming a…
-

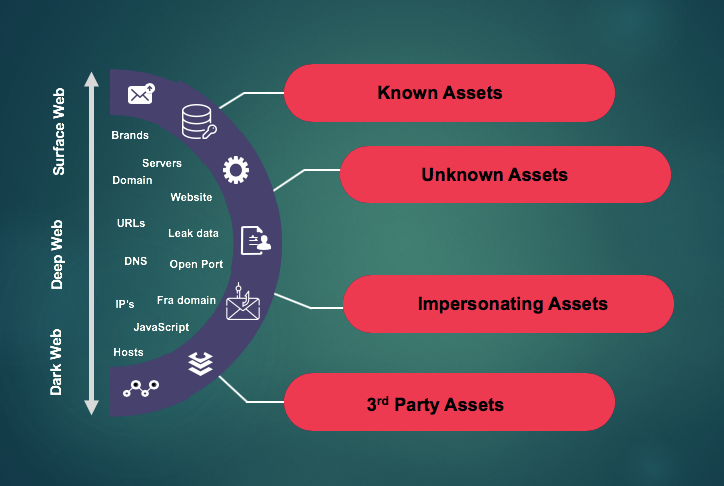
Mastering Attack Surface Management
Cyber threats are escalating and evolving at an overwhelming rate, making the security of systems and data a top priority for organizations worldwide. This necessitates the need for effective strategies to counter these threats, one of which is Attack Surface Management (ASM). This comprehensive article explores the concept of ASM, its significance in cybersecurity, its…